Privileged access management
Securing cloud identities and permissions starts with gaining deep visibility into which accounts have access to, or can take action upon, which specific resources. Prisma Cloud analyzes permissions on public CSPs to determine net-effective permissions and rightsized permissions recommendations.
-
Manage cloud entitlements from a single solution
Gain integrated capabilities from Prisma Cloud that extend resource-level posture management to cloud identities.
-
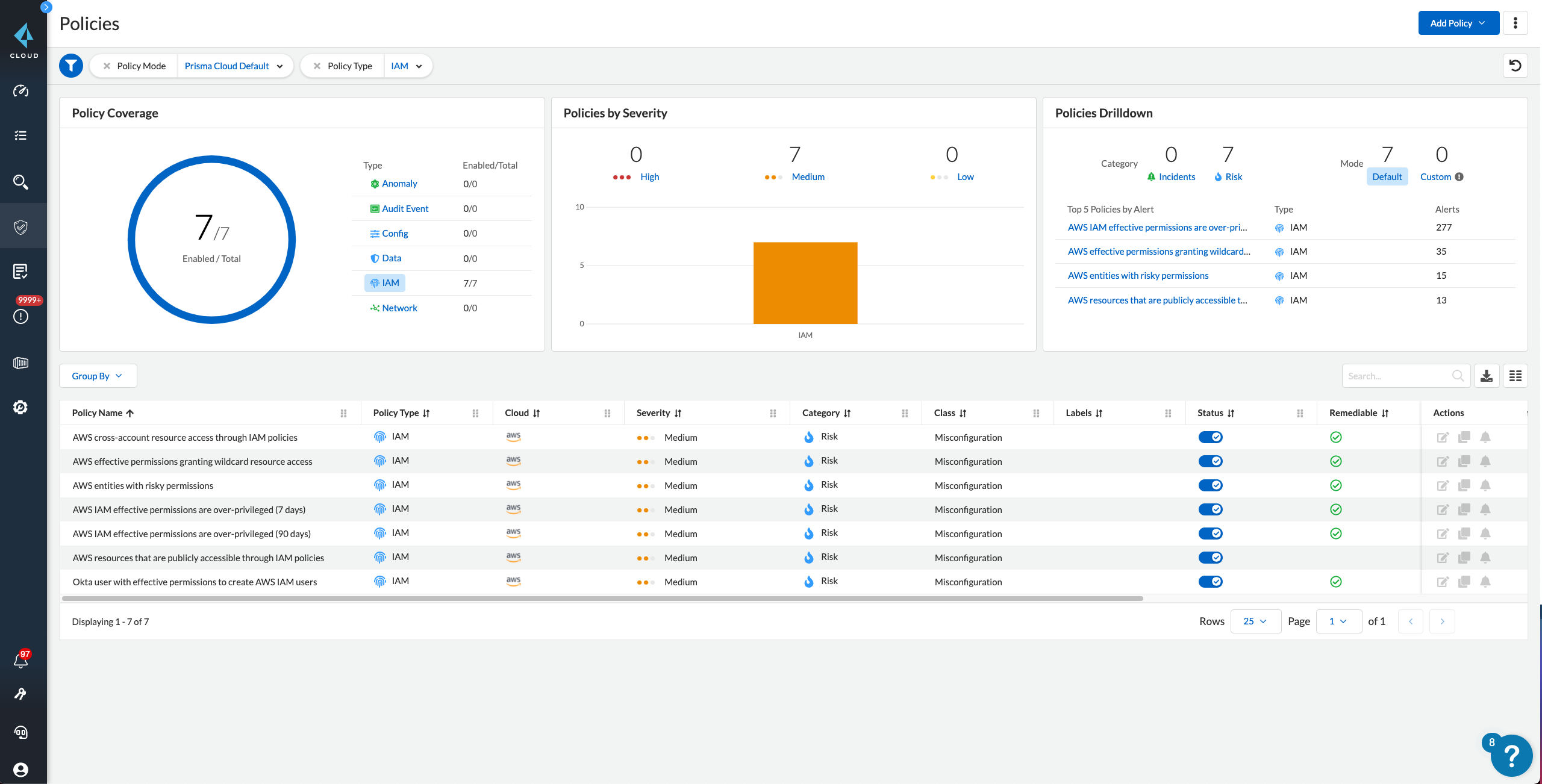
Implement pre-built policies
Leverage specialized out-of-the-box policies to detect risky permissions and remove unwanted access to cloud resources.
-
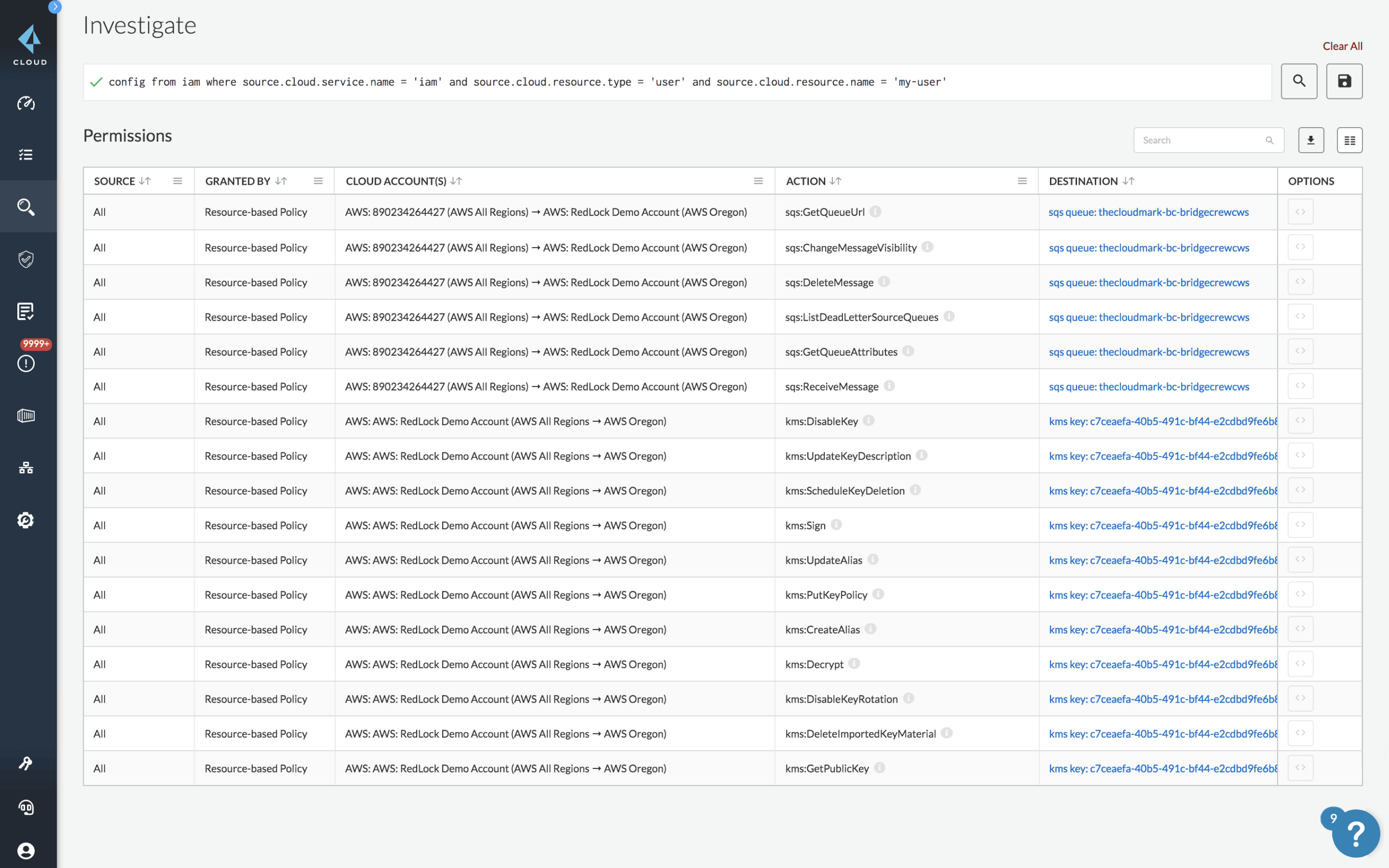
Investigate IAM entitlements
Use Resource Query Language (RQL) to see real-time and historical data to understand precisely who can take what actions on which resources, across cloud accounts.
-
Audit permissions for internal compliance
Quickly audit cloud permissions with related user data, service data and cloud accounts.