Net-effective permissions
Gain deep visibility into who has the ability to take what actions on which resources. By running complex calculations that analyze permissions such as AWS IAM roles, policies and groups; or Azure role assignments including security principals, role definitions and scopes; the CIEM module can precisely determine net-effective permissions.
-
Manage multi-cloud entitlements from a single solution
Gain integrated multi-cloud capabilities delivered from Prisma Cloud that extend everything we do for Cloud Security Posture Management (CSPM) to cloud identities.
-
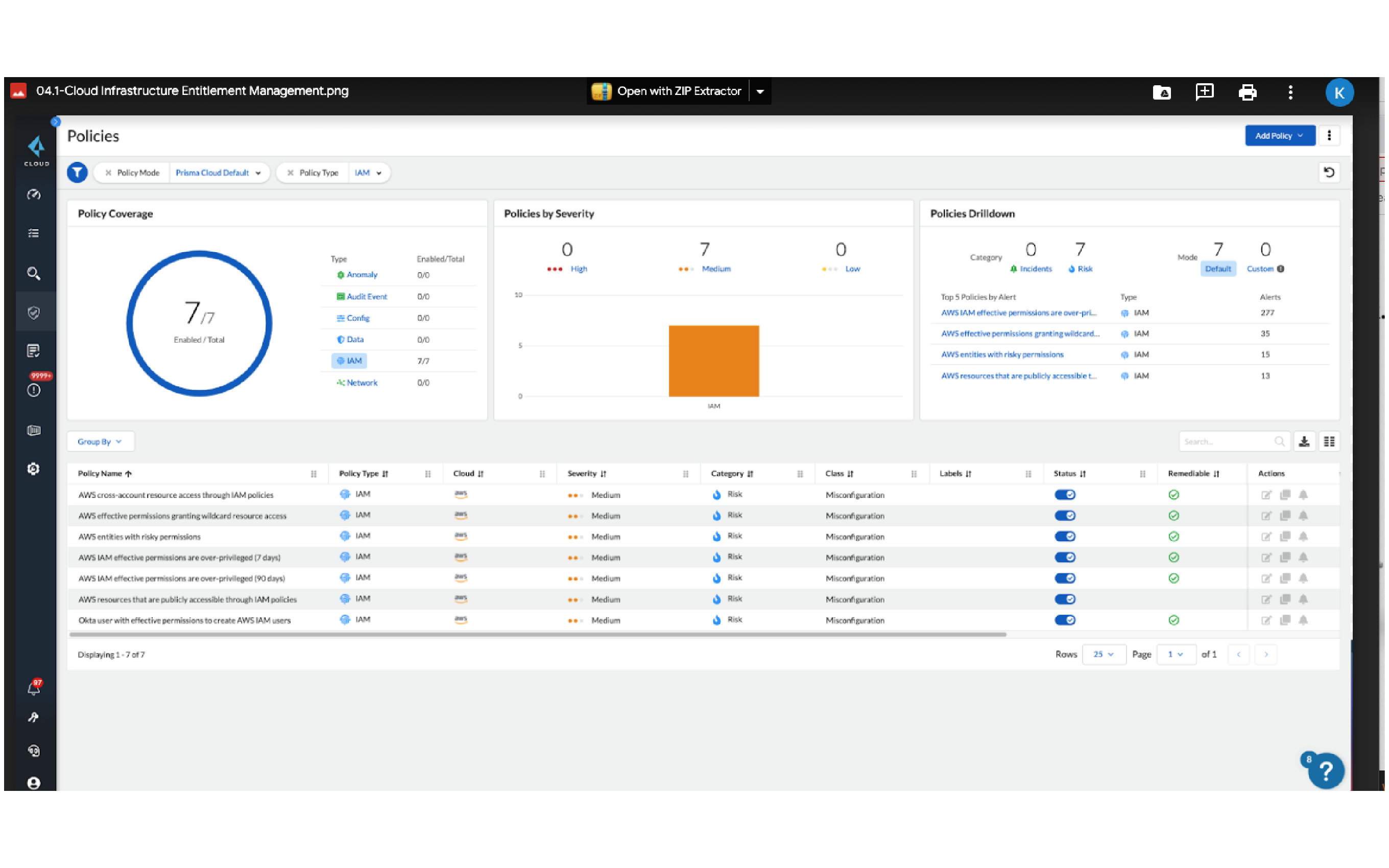
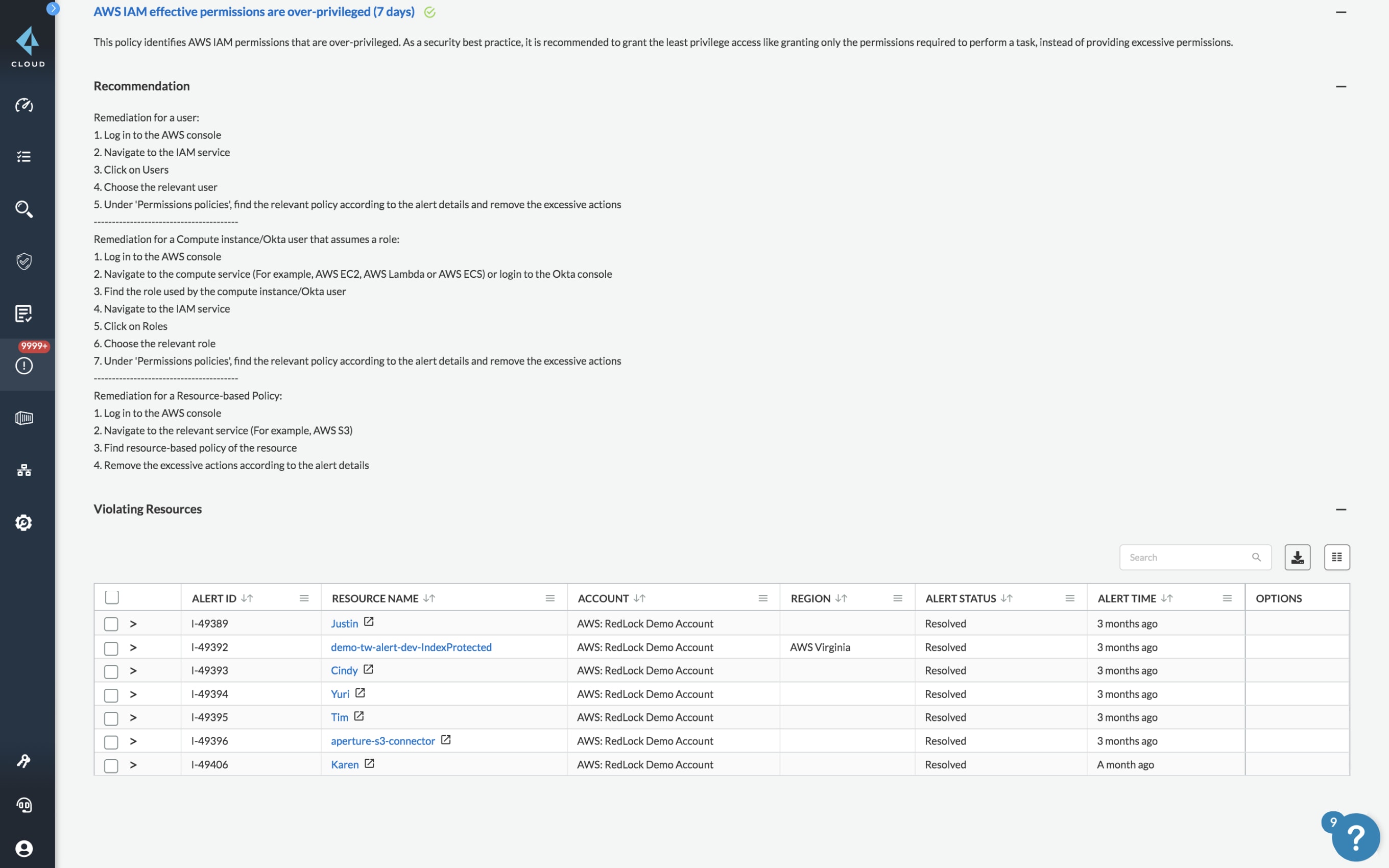
Implement pre-built policies
Leverage specialized out-of-the-box policies to detect risky permissions and remove unwanted access to cloud resources.
-
Audit permissions for internal compliance
Quickly audit cloud permissions with related user data, service data and cloud accounts.